SpaceRocketIaC is an Infrastructure as Code (IaC) solution for provisioning AWS resources to host a secure web application in a Docker container on an EC2 Ubuntu instance using Packer, Terraform, and Ansible. This tutorial will guide DevOps engineers through the process of deploying an Elixir/Phoenix application from Github using SpaceRocketIaC, including setting up a custom domain name, creating SSH keys, and configuring the infrastructure. By the end, you will have a fully functional, TLS-enabled Elixir Phoenix application hosted on a custom domain with secured logs and an Application Load Balancer, all managed and version-controlled with code.
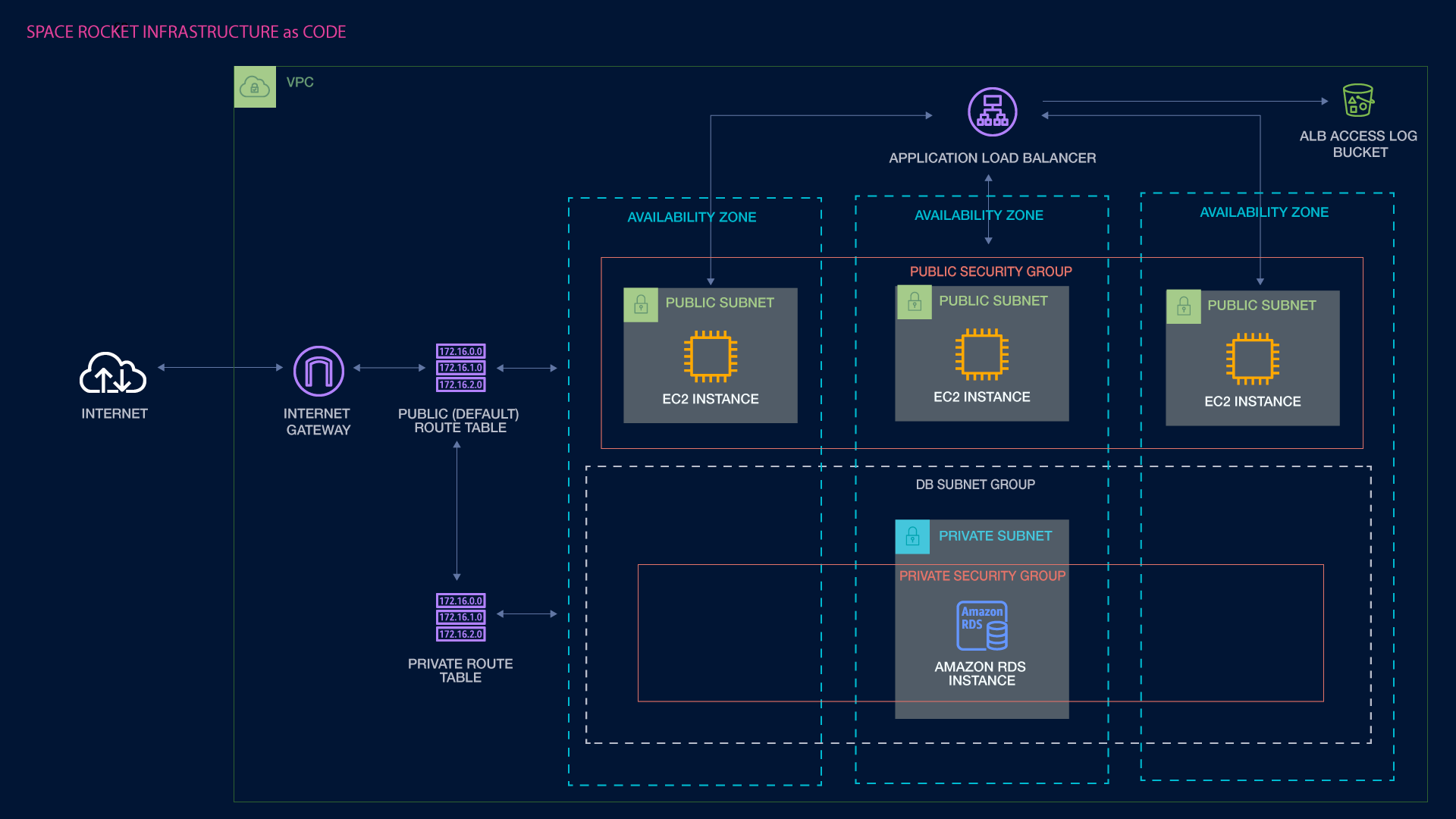
Our infrastructure will consist of a VPC with internet communication through public and private route tables, routed through an internet gateway.
Getting Started with SpaceRocketIaC
Before proceeding, ensure that you have a registered domain name (e.g. example.com) and access to its nameservers. Additionally, you should have a Cloud9 IDE instance with Terraform, Packer, and Ansible installed. For instructions on how to get started on Cloud9 IDE and install Terraform, Packer, and Ansible on it, refer to previous tutorial "Implementing Infrastructure as Code with Cloud9 IDE".
SpaceRocketIaC setup
Setting up registered domain name with Route 53
In this step, we will be configuring your custom domain name (e.g. example.com) with a 'Hosted Zone' on Route 53. To begin, navigate to the AWS console and search for Route 53. Once you are in the Route 53 dashboard, select "Hosted Zones" from the left sidebar and click on "Create Hosted Zone".
Let’s get started by navigating to the AWS console, searching for Route 53, and selecting 'Hosted zones' from the left sidebar. [Image here of AWS Route 53 console with 'Hosted zones' highlighted]
Enter your domain name and click 'Create hosted zone.' [Image here of the 'Create hosted zone' screen showing the domain name field]
Enter your domain name. [Image here of the domain name input field with a sample domain entered]
Once the hosted zone is created, retrieve the NS records. [Image here of the hosted zone details showing the NS record values]
Get the NS values from the hosted zone record.
Next, add these NS records to your domain registrar, such as name.com. [Image here of a domain registrar interface with fields for entering nameserver values]
Update the domain registrar's nameservers with the NS records.
At this point, we have a hosted zone for myexample.com on AWS Route 53, and its NS records are configured in your domain registrar's nameservers.
Fork and clone Github repo
Next, head over to the SpaceRocket-InfrastructureAsCode repository on GitHub (https://github.com/space-rocket/SpaceRocket-InfrastructureAsCode) and fork it to your own account. Once that's done, copy the HTTPS git URL from the '<> Code' button dropdown.
Next type 'git clone' and the git URL into your Cloud9IDE terminal.
git clone https://github.com/<GITHUB-USERNAME>/SpaceRocket-InfrastructureAsCode.git my_infra
Next change into the newly created directory, my_infra by typing: cd my_infra
Create a SSH key
To be able to ssh into the instances that are spun up, we will need SSH keys. You can create them with the following command:
ssh-keygen -f /home/ubuntu/.ssh/devops -t rsa
Terraform Variables Configuration
vpc_cidr = "10.123.0.0/16"
key_name = "devops_key"
public_key_path = "/home/ubuntu/.ssh/devops_rsa.pub"
private_key_path = "/home/ubuntu/.ssh/devops_rsa"
main_instance_count = 3
Note: If ssh key name is different than devops, be sure to update the public_key_path and private_key_path values.
Prod configuration
Rename prod-example.tfvars to prod.tfvars. Fill in the values that fit your project needs.
Be sure this file is not commited to the repo (its already added to .gitignore). Consider using a key vault for any of the values you see fit.
region = "us-east-1"
db_password = "SecretPassword"
db_name = "my_app_db"
db_user = "my_app_db_user"
main_domain_name = "example.com"
git_url = "https://github.com/space-rocket/my_app.git"
deploy_demo_docker = false
deploy_my_app = true
has_db = true
cloud9_ip = "12.34.56.187/32"
The background settings are as follows:
- region: The AWS region to launch your infrastructure in.
- db_password: A password used for database authentication.
- db_name: The name of the database.
- db_user: The user of the database.
- main_domain_name: The main domain name of a website, ie: example.com.
- git_url: The Git URL of the app you wish to deploy. Note for your app to be deployed, deploy_my_app has to be set to true.
- deploy_demo_docker: A boolean (true/false) Set to true to deploy a demo Docker container.
- deploy_my_app: A boolean value indicating whether to deploy your app from the git_url provided.
- has_db: A boolean value indicating whether a database is needed.
- cloud9_ip: The Elastic IPv4 address for the Cloud9 IDE environment in CIDR notation, ex: xxx.xxx.xxx.xxx/32. See previous article on how to set up Cloud9 IDE.
Usage
Build the base Ubuntu AMI.
cd packer
packer init aws-ubuntu.pkr.hcl
Run the packer build command
packer build aws-ubuntu.pkr.hcl
Once packer has completed building the AMI, you'll be able to see your very own, private, SpaceRocketUbuntu AMI.
Run Terraform commands
First, run Terraform init command.
terraform init
Run the plan command to see what will be deployed.
terraform plan -var-file="prod.tfvars"
Note: To just test things out, you can start with deploying the demo docker container by setting deploy_demo_docker to true and deploy_my_app and has_db to false
Once that looks good, go ahead run Terraform apply with --auto-approve flag.
terraform apply -auto-approve -var-file="prod.tfvars"
When completed visit your domain name and see the demo application.
Next Steps
Now that we have successfully deployed the resources needed to run a web application inside a Docker container, the next step is to automate the process of building the Docker image and deploying it to our EC2 instances. This can be done by using tools like Jenkins or AWS CodeBuild.
Conclusion
SpaceRocketIaC is an efficient IaC solution for provisioning and deploying web applications on AWS. This tutorial provided a guide on using SpaceRocketIaC to set up a custom domain, create SSH keys, and configure the infrastructure. By using SpaceRocketIaC, we can streamline the process of deploying and managing web applications while maintaining version control and security. Feedback is welcome, if you have any issues or suggestions please open an issue on Github. Also, I am available for hire. Thank you for reading!
Launch Your Project
Get your project off the ground
with Space-Rocket!
Fill out the form below to get started.